SCIM Setup
-
SCIM makes user data more secure and simplifies the user experience by automating the user identify lifecycle management process. With the addition of SCIM integration, user identifies can be created directly in a tool such as OKTA or Azure. Since it is a standard, user data is stored in a consistent way and can be communicated between the user management system and KloudHybrid. This enables IT departments to automate the provisioning/deprovisioning process while also having a single system to manage permissions and groups. Since user data is transferred automatically and communicated between the two systems, risk of errors is reduced.
-
Currently, KloudHybrid supports the following features when integrated with SCIM:
- Create users: Users in OKTA that are assigned to the KloudHybrid app will automatically be created in KloudHybrid.
- Update user attributes: Any changes to users in OKTA will automatically be made to the associated KloudHybrid user.
- Deactivate users: Users deactivated in OKTA or un-assigned from the app will be disabled in KloudHybrid.
-
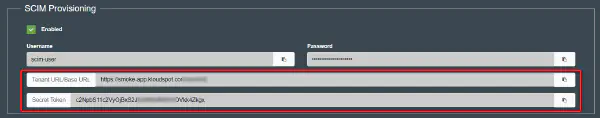
Obtain the Provisioning API credentials from KloudHybrid. In the ‘Advanced’ user interface, go to Configuration -> Integrations -> External Authentication. Enable SCIM Provisioning and click save.
NOTE: A random password will be generated by the system. You can either use the default username and password or create your own.

- Configure SCIM in either OKTA or Azure, see the sections below for instructions.
Enabling SCIM in OKTA
- The System for Cross-domain Identity Management (SCIM) specification is a provisioning protocol to create, retrieve, update, and deactivate users and groups between Okta and Hybrid application.
- To enable SCIM in OKTA. Follow the steps below.
- Navigate to Advance Settings and then go to Configuration > Integrations > External Authentication.
- Make sure OKTA is selected in the provider and SAML 2.0 in the protocol.

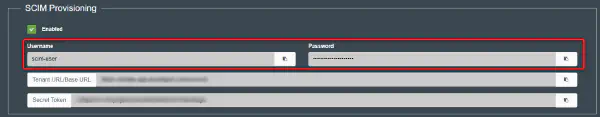
- Scroll down and enable SCIM provisioning. In the text box that opens, enter Username and Password. And save the changes.
Note: The username and password are decided by you and the Tenant URL and Secret token will be generated accordingly.

- After saving the changes. Log out of the Hybrid app and double-check that the single sign on button is functional.

- Then log in to your OKTA account.

- Click on Applications and from the drop-down select Applications.

- Select the same application that was created when the single sign-on button was integrated. Refer Configure SAML with OKTA section for more details.

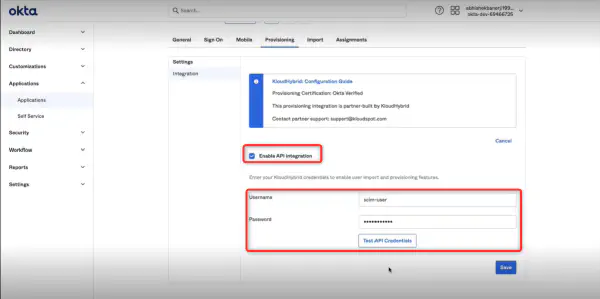
- In the window that opens, click on the Provisioning tab. And click Configure API Integration button.

- Check the Enable API integration, then in the text box that opens, enter the same username and password that you entered in the Hybrid Advanced settings.
-
Then click on the Test API Credentials button to verify the Application.
-
Once verified, you will be notified that the application has been verified successfully. If not, double-check the single sign-on configuration.
-
Refer Configure SAML with OKTA section for more details.
-
If it is working fine Click Save button.

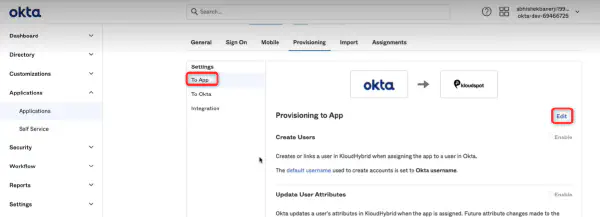
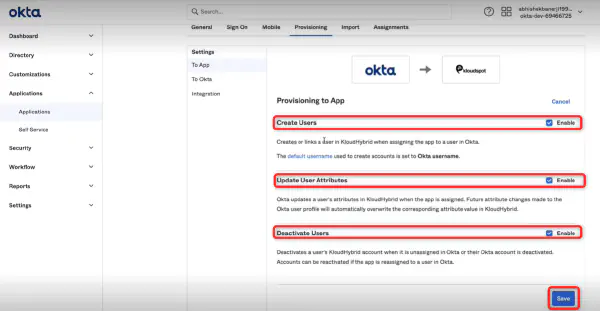
- Then navigate to To App > Edit and check the three check boxes and click Save.
Note: Only the To App option is currently operational. This means that users who add to the OKTA application will also be added to the hybrid application.
- SCIM in OKTA is added successfully.
Enabling SCIM IN Azure
- To enable SCIM in Azure. Follow the steps below.
- Navigate to Advance Settings and then go to Configuration > Integrations > External Authentication.
- Make sure Microsoft is selected in the provider and SAML V2.0 in the protocol.

- Scroll down and enable SCIM provisioning. In the text box that opens, enter Username and Password. And save the changes.
Note: The username and password are decided by you and the Tenant URL and Secret token will be generated accordingly.

- After saving the changes. Log out of the Hybrid app and double-check that the single sign on button is functional. If functional continue with steps below. Otherwise refer Configure SAML with Microsoft Azure AD section for configure SAML with Microsoft.

-
Log in to your Microsoft Azure portal on https://portal.azure.com/
-
Click on Azure Activity Directory from the Azure services options as shown below.

- Locate and click on the Enterprise Applications on the Window.

- Select the same application that was created when the single sign-on button was integrated.

- Then click on the Get Started button from the Provision User Account.

- openAgain, click on Get started button from the window that open.

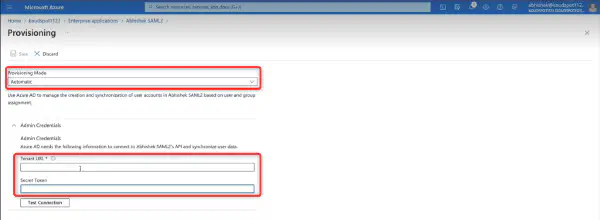
- Select the Automatic provisioning mode from the drop-down list. Then copy and paste the Tenant URL and Secret Token from the Hybrid Advanced settings.
-
Then Click on Test Connection button to authorize the connection.
-
Once authorized, you will be notified that the credentials have been authorized successfully. If not, double-check the single sign-on configuration. Refer Configure SAML with Microsoft Azure AD for more details.
-
Click on Save button.

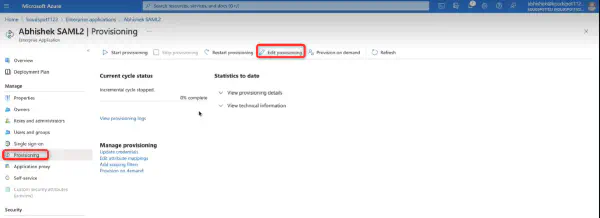
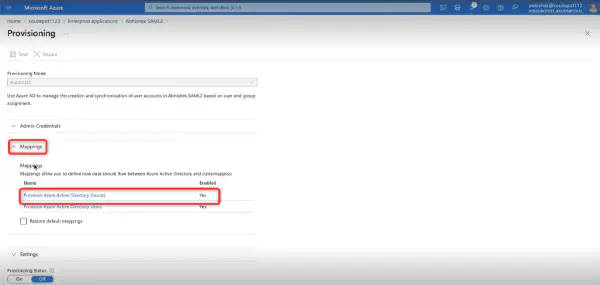
- Then navigate to Provisioning > Edit Provisioning > Mappings > Provision Azure Active Directory Groups.
- Disable it and click Save.
Note: Only newly created user information will be added to the hybrid automatically. No new groups will be added.

-
Then click on Azure Active Directory Users. Make sure Create, Update and Delete are enabled in the target object actions.
-
Click on Save button. SCIM in Microsoft Azure is added successfully.