Connecting to your Infrastructure
-
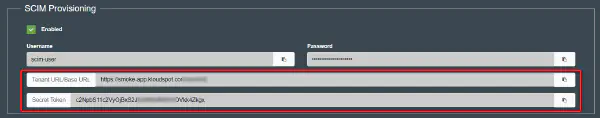
Once you have successfully created your hybrid office in KloudHybrid, the next crucial step is to establish seamless connectivity between KloudHybrid and your existing infrastructure. This enables the application to efficiently interact with your established systems and streamline various processes.
-
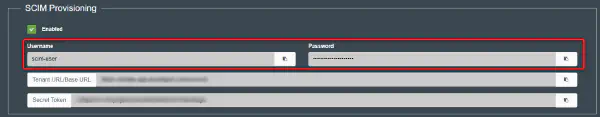
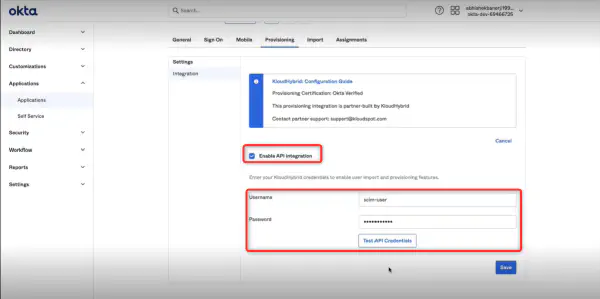
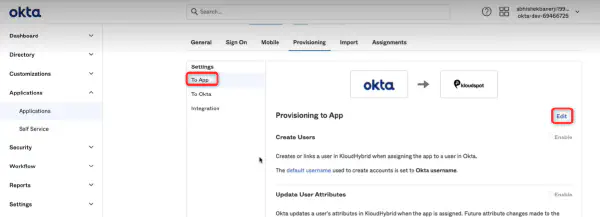
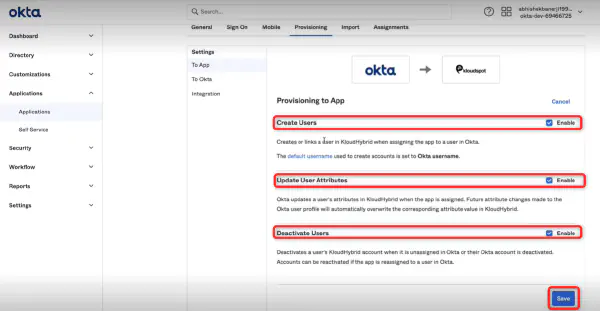
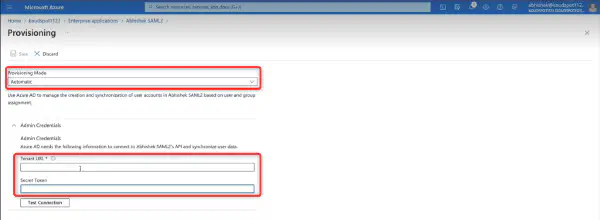
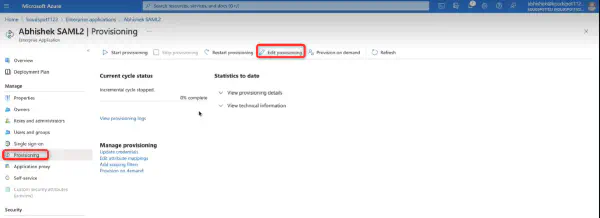
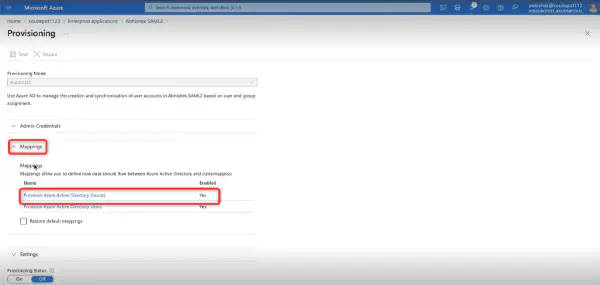
KloudHybrid offers two providers, namely OKTA and Microsoft, for establishing this connection. You can choose the provider that aligns best with your organization’s requirements and infrastructure.
Overview
In this Section, we will explore various aspects of establishing connections to your infrastructure, ensuring seamless integration and communication within your systems. We will cover essential topics such as SCIM setup, Microsoft Graph API integration, email (SMTP) setup, SMS setup, application integrations, external authentication, and other valuable integrations. Whether you’re looking to streamline your operations or enhance the functionality of your infrastructure, this section will provide you with the necessary insights and instructions to successfully connect your systems and optimize your workflows.